Self-Hosting Tesseral
Self-hosting Tesseral is a very advanced use-case, and we are still working on making the process of self-hosting easier.
If you are self-hosting Tesseral, please reach out to us at
support@tesseral.com. We will help you get this done, and help make sure your
deployment is secure.
Tesseral is an open-source project that you can self-host on your own infrastructure. This document describes how you can do that.
Tesseral Architecture
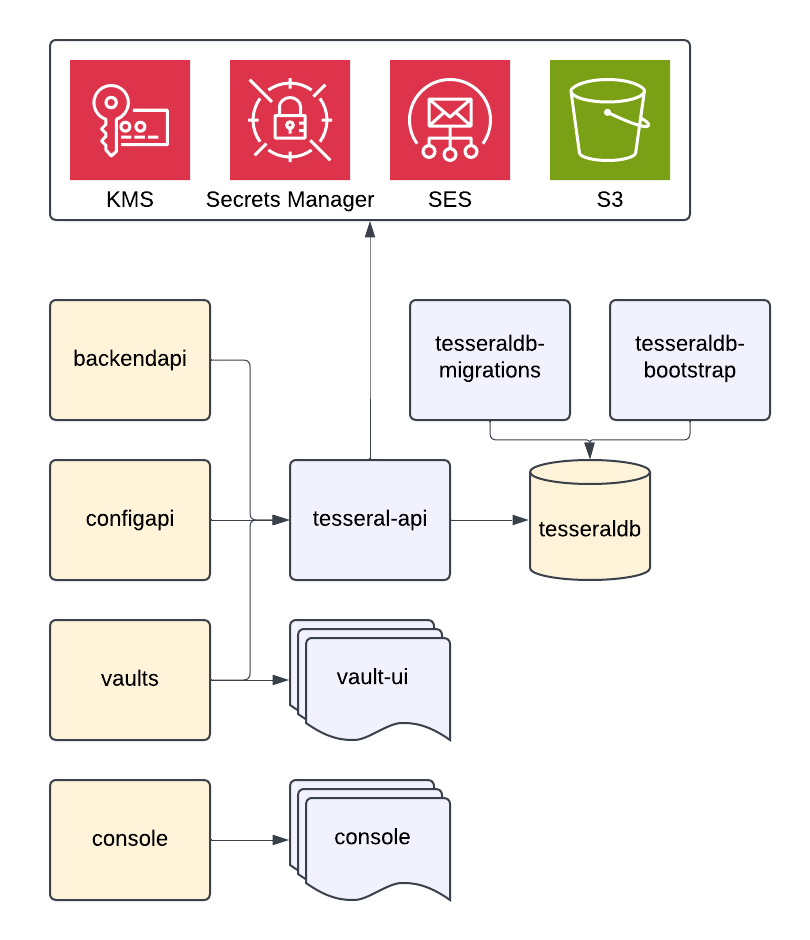
Tesseral provides four artifacts that you can self-host:
-
tesseral-apiis a binary that represents the entire Tesseral backend codebase. -
vault-uiis a set of HTML, CSS, and JavaScript for the UI elements of Vaults. -
consoleis a set of HTML, CSS, and JavaScript for the Tesseral Console. -
tesseraldb-migrationsis a set of database migrations for the Tesseral database. -
tesseraldb-bootstrapis an initialization script to initialize the Tesseral database after migrating it.
When you deploy Tesseral, you are responsible for managing the following infrastructure:
-
backendapiis the Tesseral Backend API, a reverse proxy that talks totesseral-api. The hosted version of Tesseral runs this atapi.tesseral.com. -
confgapiis the Tesseral Config API, a reverse proxy that talks totesseral-api. The hosted version of Tesseral runs this atconfig.tesseral.com. -
vaultsis the set of Tesseral Project Vaults, each of which is a reverse proxy that talks totesseral-apior serves thevault-uiSPA, depending on the request path. -
consoleis a the Tesseral Console, a reverse proxy that serves theconsoleSPA. -
tesseraldbis a PostgreSQL database.
The rest of this section describes these components in greater detail.
To follow these instructions, you must get a copy of the Tesseral source code, available from GitHub at:
AWS Infrastructure
Tesseral requires a set of AWS services. You do not need to run tesseral-api
or any other software component of Tesseral in AWS, but you do need to ensure
tesseral-api has access to the following AWS services:
-
AWS Secrets Manager is optional but strongly recommended as a place to keep any secret environment variables
tesseral-apirequires. -
AWS Key Management Service is a required, and is used to encrypt session signing keys and OAuth client IDs.
-
Amazon Simple Email Service is required for sending email verification codes to end users.
-
Amazon S3 is required for storing user content, such as Project logos.
tesseral-api
tesseral-api is distributed as a binary, written in Golang. To build this
binary for your operating system and architecture, you must first install Golang
and then run:
This will produce an api binary. For documentation on the environment
variables api takes, run api --help. The most important environment
variables are:
vault-ui
vault-ui is distributed as a set of static files. To build these files, run:
This will produce the files to serve to vault-ui/public.
console (Single-Page Application)
console is distributed as a set of static files. To build these files, you
will first need to run tesseral-bootstrap. Then run:
This will produce the files to serve to console/public.
tesseraldb-migrations
To prepare the database tables in tesseraldb, you will need to install
golang-migrate. Then run:
Where postgres://... is a connection string to tesseraldb.
tesseral-bootstrap
After having run tesseraldb-migrations, you must run tesseral-bootstrap to
initialize a “dogfood” project. This is a special initial project that Tesseral
uses to authenticate users of the Tesseral Console.
For these parameters:
-
Have
--databasepoint totesseraldb. -
Have
--root-user-emailbe an email address you have access to. -
session-kms-key-idshould be the same value you use forAPI_SESSION_KMS_KEY_IDintesseral-api. -
console-domainshould be the same value you use forAPI_CONSOLE_DOMAINintesseral-api. -
vault-domainshould be the domain name of the vault you want to use for the initial, dogfood project. This must be a subdomain ofconsole-domain. In the hosted version of Tesseral, this isvault.console.tesseral.com.
backendapi
backendapi must be a reverse proxy (e.g. an nginx, a Cloudflare worker, an AWS
Cloudfront distribution or API Gateway) that:
- Is available from the public internet.
- Serves HTTPS.
- Performs no caching.
- Forwards all requests to
tesseral-api, but prepends/api/backendto all request paths.
As a non-normative starting point, an nginx configuration for this may look like:
configapi
configapi must be a reverse proxy (e.g. an nginx, a Cloudflare worker, an AWS
Cloudfront distribution or API Gateway) that:
- Is available from the public internet.
- Serves HTTPS.
- Performs no caching.
- Forwards all requests to
tesseral-api, but prepends/api/config-apito all request paths.
As a non-normative starting point, an nginx configuration for this may look like:
vaults
Tesseral is multi-tenant software; every self-hosted deployment of Tesseral
supports running multiple Projects at once. Every Tesseral Project has a Vault,
and each of these Vaults (collectively referred to as vaults in this article)
must point at the same reverse proxy.
How you achieve this architecture is up to you; in the cloud-hosted version,
Tesseral operates a wildcard subdomain (*.tesseral.app) for
“Tesseral-generated” subdomains, as well as a proxy supporting user-provided
domains.
vaults must be a reverse proxy (e.g. an nginx, a Cloudflare worker, an AWS
Cloudfront distribution or API Gateway) that:
- Is available from the public internet.
- Serves HTTPS.
- Forwards, without caching, all requests beginning in
/apior/.well-knowntotesseral-api. - Serves a single-page application for all other requests, serving the contents
of
vault-ui. All 404s must serveindex.html.
console (Reverse Proxy)
vaults must be a reverse proxy (e.g. an nginx, a Cloudflare worker, an AWS
Cloudfront distribution or API Gateway) that:
- Is available from the public internet.
- Serves HTTPS.
- Serves a single-page application for all requests, serving the contents of
vault-ui. All 404s must serveindex.html.
tesseraldb
tesseraldb must be a PostgreSQL database or cluster, running version 16.4 or
later. tesseraldb-migrations and tesseral-bootstrap both require one-off
access to this database; thereafter, only tesseral-api needs to have network
connectivity to this database.
Using Tesseral SDKs
Tesseral’s clientside and serverside SDKs default to using the cloud-hosted version of Tesseral. All of Tesseral’s SDKs support overriding this configuration to use your self-hosted instance instead.
For the Tesseral React SDK, override the configapi domain (default:
config.tesseral.com) using the configApiHostname parameter on
TesseralProvider:
For all backend SDKs, override the backendapi domain (default:
api.tesseral.com) by providing an additional parameter when constructing a
client instance: