Users in Tesseral
What is a User?
If you make B2B SaaS, your customers are companies — or similar entities, such as schools or nonprofits. Tesseral represents each of these companies as an Organization.
However, individuals who work at companies still need to log into and use your software. Tesseral represents each such individual as a User.
Tesseral is designed for use in business software, so it always uses B2B multitenancy model. Each User always belongs to exactly one Organization. Because each Organization always belong to exactly one Project, each User must therefore belong to exactly one Project.
For example, suppose Jane Doe and John Smith both work at AcmeCorp and use your application. You will have an Organization for AcmeCorp. You will have one User record for Jane Doe and another for John Smith; both of these user records will belong to the Organization record for AcmeCorp. If AcmeCorp belongs to the MyApp Production project, then both User records — for Jane Doe and John Smith — therefore belong to the MyApp Production project.
Properties of Users
Users in Tesseral directly relate to the following concepts:
- Organizations
- Sessions
- Passkeys
Each User has the following top-level properties:
- ID
- Organization ID
- Create Time
- Update Time
- Owner
- Google User ID
- Microsoft User ID
- Has Authenticator App
Related concepts
Users and Organizations
Each User record always belongs to exactly one Organization record.
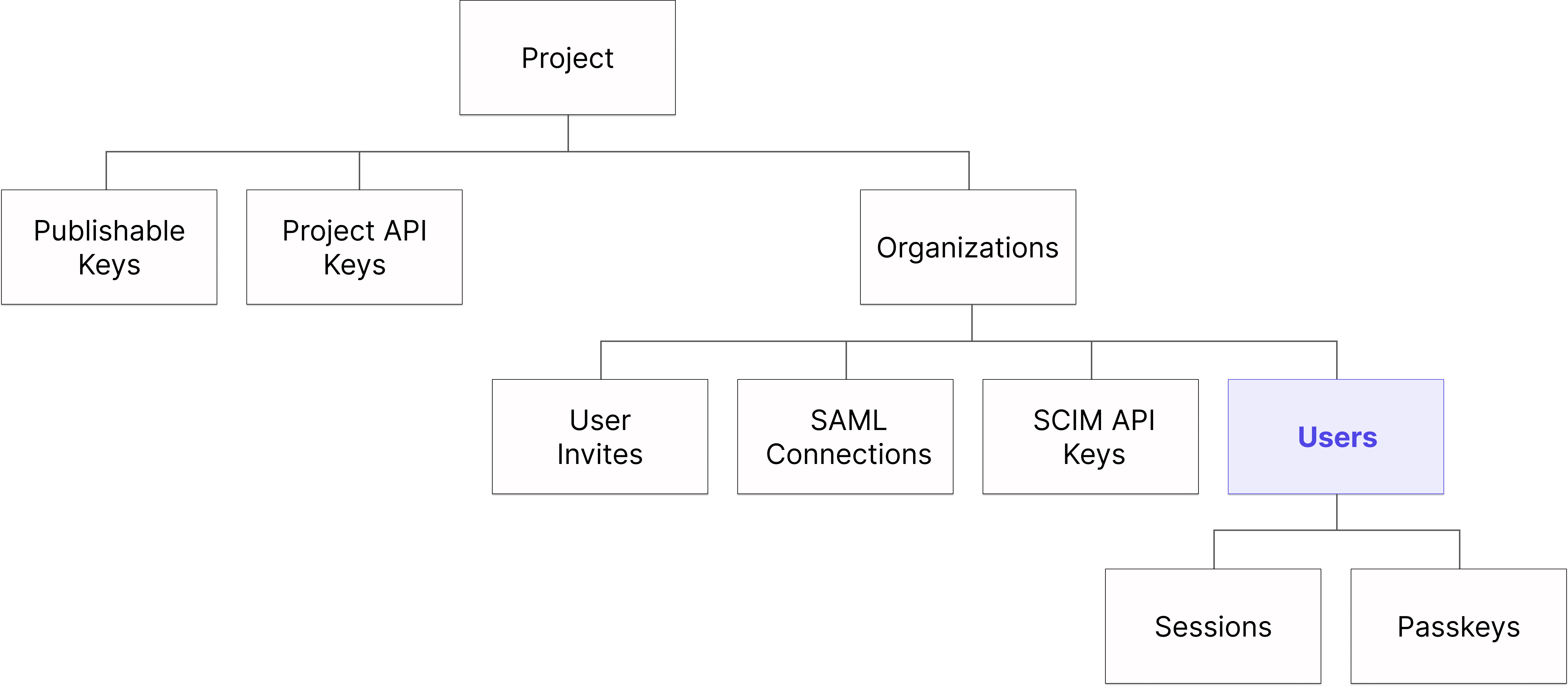
Learn more about the relationship between Users and Organizations and Tesseral’s B2B multitenancy model.
Users and Sessions
Each time a given User successfully logs in, Tesseral creates a Session in the console. to mark the User’s authentication status.
Sessions are very simple. They consist of the following data:
Each User may (and generally will) have many Sessions. A Session always belongs to exactly one User.
id of a session is not a secret. It is not a session token. You can freely use the id of a session without worrying about attackersUsers and Passkeys
Passkeys are a secondary authentication factor in Tesseral. They make possible a particular kind of multifactor authentication (MFA).
A User may have many Passkeys. Each Passkey always belongs to exactly one User.
Top-level properties of Organizations
ID
Each User record has a universally unique identifier in Tesseral called id. This identifier always starts with the prefix user_. For example, user_e6hixknsu0gww708mssi7d846 is an id for a User in Tesseral.
Organization ID
Every User in Tesseral belongs to exactly one Organization. organization_id is the unique identifier for the Organization that a given User belongs to.
Each User in Tesseral must have a verified email address, which gets captured in the email field. This also serves as a human-legible identifier for the User.
Create Time
Identified in the Backend API as createTime, this field simply represents the timestamp from when the User record was created.
Update Time
Identified in the Backend API as updateTime, this field represents the timestamp from the last change to the User record’s properties.
Owner
Each User may either be an owner or not an owner. If a User has owner set to
true (displayed as Yes), then the User is an owner.
Owners of an Organization have broad administrative control over their Organization. Owners can make certain changes to their Organization that other Users cannot make. Specifically, an owner can:
- Create User Invites
- Edit login methods enabled for the Organization
- Configure SCIM provisioning for the Organization, if SCIM provisioning is enabled.
- Modify Organization-Specific Roles for the Organization, if custom Roles are enabled.
- Remove Users from their Organization.
- Edit whether other Users are Owners.
When using Role-Based Access Control, owners have all Actions enabled.
Google User ID
If a User uses Login with Google, Google supplies Tesseral with certain data about the person logging in. Among that data, Google shares a unique identifier with Tesseral called sub that looks something like 10769150350006150715113082367. You can read more about this identifier in Google’s documentation.
Tesseral stores this identifier as the Google User ID for the User.
Microsoft User ID
If a User uses Login with Microsoft, Microsoft supplies Tesseral with certain data about the person logging in. Among that data, Microsoft shares a unique identifier with Tesseral called oid that looks something like 12345678-90ab-cdef-1234-567890abcdef. You can read more about this identifier in Microsoft’s documentation.
Tesseral stores this identifier as the Microsoft User ID for the User.
sub claim for Microsoft as it does for Google. Microsoft and Google logins work differently under the hood.Has Authenticator App
Tesseral supports use of authenticator apps (e.g., Okta Verify) for multifactor authentication (MFA).
Users must configure authenticator apps themselves. They may do so at your Vault Domain under User Settings.
When a User has successfully configured an authenticator app, the User’s hasAuthenticatorApp property will be set to True (displayed as Enabled). Otherwise, hasAuthenticatorApp will be set to False (displayed as Not Enabled).